Abstract
- A form of Software Interrupt that allows Process (进程) in User Space to request privileged services like hardware access from the Kernel
Better Security
Since privileged services are carried out by the kernel, kernel can enforce security implementation. This prevents programs from doing malicious stuff.
System Call Mechanism
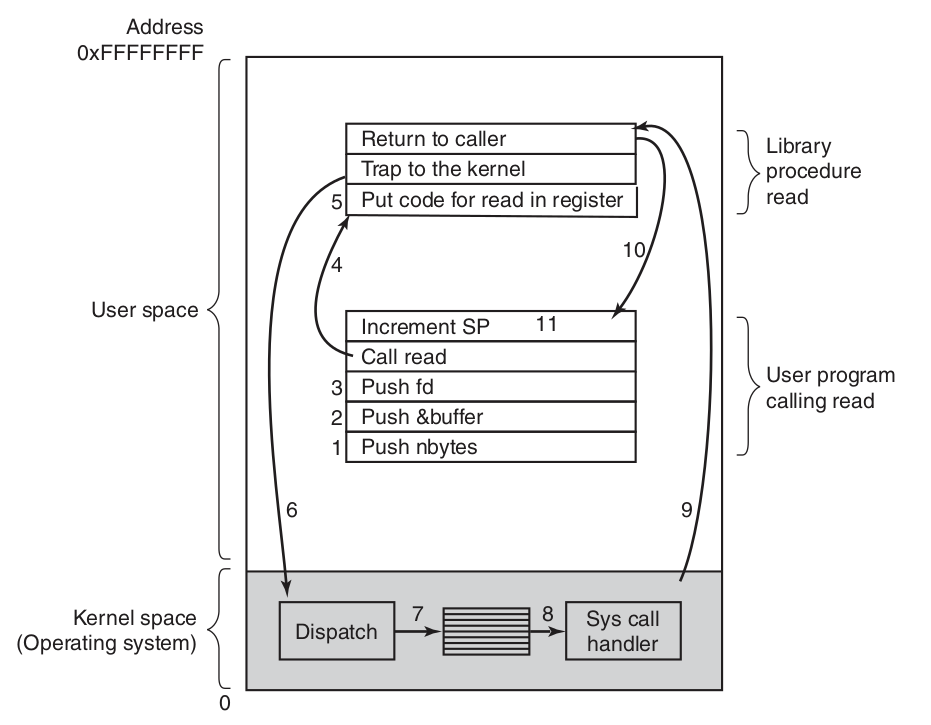
Step 1-3: Calling Process (进程) pushes the arguments for the parameters of the system call to its Stack Segment
Step 4(the start of Library Call): An Instruction is triggered to trigger the corresponding Library Call, the same instruction is used to trigger other library calls
Step 5 Library Call puts system call interrupt number in a place where Kernel expects it, such as a Register
Step 6: Execute Trap Interrupt (陷入) to enter the Kernel Mode and start execution at a fixed address within the kernel
Step 7: The kernel codes known as dispatcher following the trap interrupt examines system call interrupt number, dispatch the correct Interrupt Handler via Interrupt Vector Table
Step 8: The desired Interrupt Handler starts running
Step 9: After the interrupt handler finishes, control is returned to the library call at the Instruction following the Trap Interrupt (陷入)
Step 10: Then, library call returns, and we are back to the user program
Step 11: To finish the job, the process needs to remove the library call related data like the arguments we pushed to the stack segment from its stack segment by incrementing the Stack Pointer
System call & process management
Control is passed back to the Kernel when a system call is made by the Process (进程). Kernel uses this opportunity to perform its Process Scheduling. If the process hogs to the CPU and doesn’t make any system call, we have Preemptive Scheduling to handle this.
Tip
The system calls made by a process can be traced by
strace.
System Call is ISA-dependent
- The actual mechanics of issuing a system call are highly Instruction Set Architecture (ISA) dependent and often must be expressed in Assembly language. For example, some ISA may expect the parameters be stored in Stack Segment of the Kernel, some ISA may expect the parameters be stored in Register
Solution: abstraction!
We have Abstraction Barrier built on top of these System Call (系统调用) in the form of Library Call that follows a standardised interface like POSIX by wrapping the Assembly Instruction of different ISAs. Specific ISA Instruction is generated during Compilation automatically.
This makes it possible for user programs like OS System Program to make system call that requests privileged services from the kernel regardless of the underlying ISA - user program is communicating with library call directly and communicating with system call indirectly!
Important
Program should always check the results of Library Call to see if an error has occurred.
Linux System Call

- Above is a standardised set of Library Call that wraps System Call (系统调用), almost 1-to-1. Here is a full list
Windows System Call

- The list above shows the Library Call which is powered by Windows’ System Call (系统调用)
