Abstract
- A Cloudflare security service that allows you to set up policies and rules that let you define who can or cannot access your applications based on user Identity, network attributes, and device posture
- You can access the dashboard at Cloudflare Access
Access protected website via a temporary token
We can obtain a JWT token which authenticates HTTP Request sent to the websites that are protected by Cloudflare Access. Use
cloudflared access login <your_website_endpoint>to generate atemporary_token. Then you can access the website usingcurl -H "cf-access-token: <temporary_token>" <your_website_resources>, the flag-Oflag downloads the resource as a file to your local machine.Refer to Cloudflare Zero Trust docs for more details.
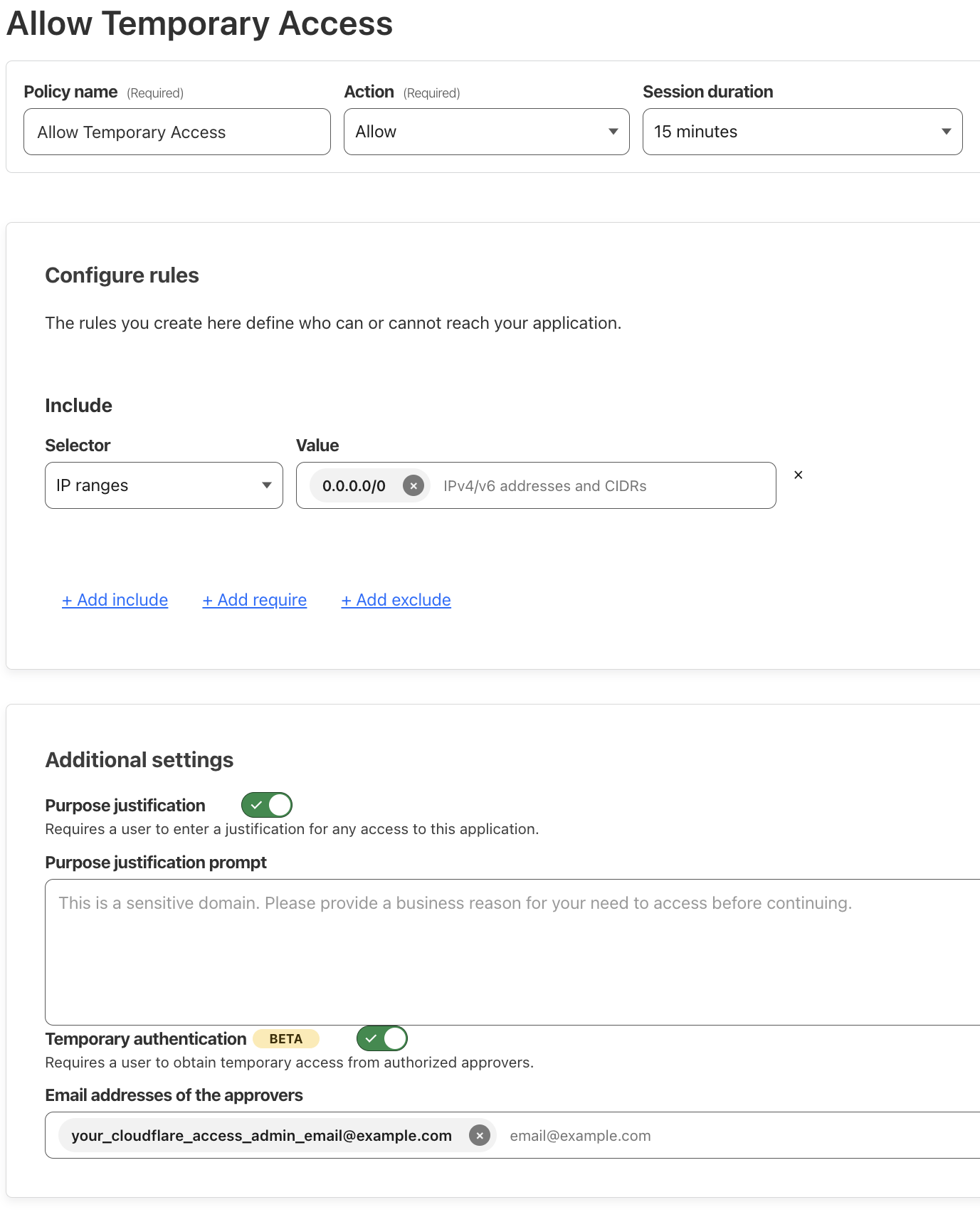
Cloudflare Access Temporary Authentication
- Users are required to proof their identity first, then obtain approval from application administrator before they can access a specific application
- The administrator will receive an email notification with the user identity to approve or deny the request. Unlike a typical Allow policy, the user will have to request access at the end of each session. This allows you to define the users who should have persistent access and those who must request temporary access
- Refer to Cloudflare Access - Temporary authentication for setup guide
Email addresses of the approvers
Make sure you setup App Launcher · Cloudflare Zero Trust docs and create a policy that authenticate the emails of the approvers, or there is no way for you to approve the temporary authentication request
And you need a different approver email to approve temporary authentication for another approver email!
Allow Temporary Authentication Policy Example
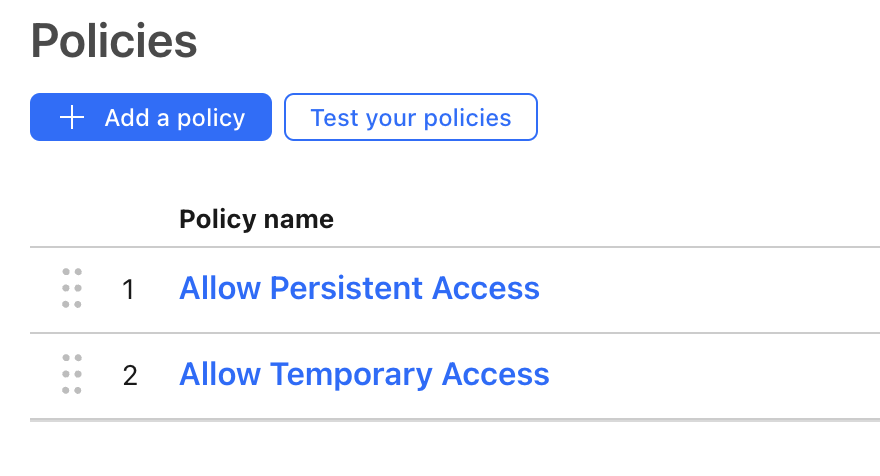
Allow some users to access without approval
You can optionally add a second Allow policy for users who should have persistent access (Access without the need to get approved). But make sure this second allow policy is placed above the temporary authentication policy, an example is shown below